C:\Users\r\Desktop\kdfe>kdfe.cmd "%systemroot%\Minidump\041111-13556-01.dmp"
Microsoft (R) Windows Debugger Version 6.12.0002.633 X86
Copyright (c) Microsoft Corporation. All rights reserved.
Loading Dump File [C:\Windows\Minidump\041111-13556-01.dmp]
Mini Kernel Dump File: Only registers and stack trace are available
Symbol search path is: srv*C:\symbols*
http://msdl.microsoft.com/download/symbols
Executable search path is: srv*C:\symbols*
http://msdl.microsoft.com/download/symbols
Windows 7 Kernel Version 7601 (Service Pack 1) MP (2 procs) Free x86 compatible
Product: WinNt, suite: TerminalServer SingleUserTS
Built by: 7601.17514.x86fre.win7sp1_rtm.101119-1850
Machine Name:
Kernel base = 0x82a01000 PsLoadedModuleList = 0x82b4b850
Debug session time: Mon Apr 11 01:54:09.064 2011 (UTC + 3:00)
System Uptime: 0 days 0:26:18.672
Loading Kernel Symbols
...............................................................
................................................................
...............................
Loading User Symbols
Loading unloaded module list
......
0: kd> kd: Reading initial command '!analyze -v; q'
*******************************************************************************
* *
* Bugcheck Analysis *
* *
*******************************************************************************
KERNEL_MODE_EXCEPTION_NOT_HANDLED_M (1000008e)
This is a very common bugcheck. Usually the exception address pinpoints
the driver/function that caused the problem. Always note this address
as well as the link date of the driver/image that contains this address.
Some common problems are exception code 0x80000003. This means a hard
coded breakpoint or assertion was hit, but this system was booted
/NODEBUG. This is not supposed to happen as developers should never have
hardcoded breakpoints in retail code, but ...
If this happens, make sure a debugger gets connected, and the
system is booted /DEBUG. This will let us see why this breakpoint is
happening.
Arguments:
Arg1: c0000046, The exception code that was not handled
Arg2: 82a829a0, The address that the exception occurred at
Arg3: abceb16c, Trap Frame
Arg4: 00000000
Debugging Details:
------------------
*** WARNING: Unable to verify timestamp for ULCDRHlp.sys
*** ERROR: Module load completed but symbols could not be loaded for ULCDRHlp.sys
*** WARNING: Unable to verify timestamp for PxHelp20.sys
*** ERROR: Module load completed but symbols could not be loaded for PxHelp20.sys
*** WARNING: Unable to verify timestamp for GEARAspiWDM.sys
*** ERROR: Module load completed but symbols could not be loaded for GEARAspiWDM.sys
EXCEPTION_CODE: (NTSTATUS) 0xc0000046 - <Unable to get error code text>
FAULTING_IP:
nt!KeReleaseMutant+215
82a829a0 cc int 3
TRAP_FRAME: abceb16c -- (.trap 0xffffffffabceb16c)
ESP EDITED! New esp=abceb51c
ErrCode = 00000000
eax=c0000046 ebx=878af030 ecx=871e2500 edx=00000000 esi=871e25e4 edi=00000000
eip=82a829a0 esp=abceb1e0 ebp=abceb554 iopl=0 nv up ei ng nz na po nc
cs=0000 ss=0010 ds=0023 es=0023 fs=0030 gs=0000 efl=00000282
nt!KeReleaseMutant+0x215:
82a829a0 cc int 3
Resetting default scope
CUSTOMER_CRASH_COUNT: 1
DEFAULT_BUCKET_ID: VISTA_DRIVER_FAULT
BUGCHECK_STR: 0x8E
PROCESS_NAME: firefox.exe
CURRENT_IRQL: 0
LAST_CONTROL_TRANSFER: from 82a82782 to 82a829a0
STACK_TEXT:
abceb554 82a82782 871e25e4 00000001 00000000 nt!KeReleaseMutant+0x215
abceb56c 9a1f413c 871e25e4 00000000 871f3018 nt!KeReleaseMutex+0x14
WARNING: Stack unwind information not available. Following frames may be wrong.
abceb58c 9a1f1a7f 005eb008 82a38593 871e24e0 ULCDRHlp+0x313c
abceb5ac 8b85f48c 8b86067c 871f3018 855eb008 ULCDRHlp+0xa7f
abceb5cc 82a38593 871f3018 855eb008 88284aa8 PxHelp20+0x448c
abceb5e4 8b62049c 78e1b860 abceb670 00000000 nt!IofCallDriver+0x63
abceb628 8b62bffe 00284aa8 abceb670 abceb654 Wdf01000!FxIoTarget::SubmitSync+0x198
abceb64c 8bee249a 00000020 88284aa8 871e4798 Wdf01000!imp_WdfRequestSend+0x178
abceb680 8bee226d 78e199f0 88284b80 00000000 cdrom!DeviceSendRequestSynchronously+0x9c
abceb6a0 8b644fe8 871e67d0 77d7b550 88284aa8 cdrom!CreateQueueEvtIoDefault+0x96
abceb6b8 8b6465e6 78e05490 77d7b550 88284aa8 Wdf01000!FxIoQueueIoDefault::Invoke+0x27
abceb6dc 8b6489ac 77d7b550 88284aa8 871fab68 Wdf01000!FxIoQueue:

ispatchRequestToDriver+0x533
abceb6f8 8b649a36 871fab00 00000000 855eb008 Wdf01000!FxIoQueue:

ispatchEvents+0x3be
abceb718 8b643ff4 88284aa8 855eb12c 86049918 Wdf01000!FxIoQueue::QueueRequest+0x1ec
abceb74c 8b6441f0 855eb008 871fb0d8 871e4ac0 Wdf01000!FxPkgGeneral::OnCreate+0x1c3
abceb768 8b63aa3f 855eb008 abceb78c 82a38593 Wdf01000!FxPkgGeneral:

ispatch+0xc3
abceb774 82a38593 871e4ac0 855eb008 855eb12c Wdf01000!FxDevice:

ispatch+0x7f
abceb78c 9a1f882a 88152330 871fb020 855eb008 nt!IofCallDriver+0x63
abceb7a8 82a38593 001fb020 005eb008 8815238c GEARAspiWDM+0x82a
abceb7c0 82c482a9 84c708a1 abceb968 00000000 nt!IofCallDriver+0x63
abceb898 82c27ac5 871e4ac0 8d174698 856e9330 nt!IopParseDevice+0xed7
abceb914 82c37ed6 00000000 abceb968 00000240 nt!ObpLookupObjectName+0x4fa
abceb974 82c2e9b4 abcebb00 85174698 abceb900 nt!ObOpenObjectByName+0x165
abceb9f0 82c34b3a abcebaf0 00000080 abcebb00 nt!IopCreateFile+0x673
abceba38 82a3f1ea abcebaf0 00000080 abcebb00 nt!NtOpenFile+0x2a
abceba38 82a3d561 abcebaf0 00000080 abcebb00 nt!KiFastCallEntry+0x12a
abcebac8 82c6875e abcebaf0 00000080 abcebb00 nt!ZwOpenFile+0x11
abcebb1c 8b7ab3da abcebbb8 00000080 abcebb44 nt!IoGetDeviceObjectPointer+0x59
abcebb4c 8b7abb51 85a9fe58 abcebbb8 abcebb80 mountmgr!QueryDeviceInformation+0x28
abcebb8c 8b7b1be7 85a9fe58 abcebbb8 00000000 mountmgr!FindDeviceInfo+0x3f
abcebbe0 8b7b35df 85a9fe58 8797be38 85710260 mountmgr!MountMgrQueryDosVolumePaths+0x10d
abcebbfc 82a38593 85a9fe74 006d0034 8797be38 mountmgr!MountMgrDeviceControl+0xd3
abcebc14 82c2c99f 85710260 8797be38 8797bea8 nt!IofCallDriver+0x63
abcebc34 82c2fb71 85a9fda0 85710260 00000000 nt!IopSynchronousServiceTail+0x1f8
abcebcd0 82c763f4 85a9fda0 8797be38 00000000 nt!IopXxxControlFile+0x6aa
abcebd04 82a3f1ea 00000148 00000000 00000000 nt!NtDeviceIoControlFile+0x2a
abcebd04 779d70b4 00000148 00000000 00000000 nt!KiFastCallEntry+0x12a
0574f884 00000000 00000000 00000000 00000000 0x779d70b4
STACK_COMMAND: kb
FOLLOWUP_IP:
ULCDRHlp+313c
9a1f413c ?? ???
SYMBOL_STACK_INDEX: 2
SYMBOL_NAME: ULCDRHlp+313c
FOLLOWUP_NAME: MachineOwner
MODULE_NAME: ULCDRHlp
IMAGE_NAME: ULCDRHlp.sys
DEBUG_FLR_IMAGE_TIMESTAMP: 41c9dd4d
FAILURE_BUCKET_ID: 0x8E_ULCDRHlp+313c
BUCKET_ID: 0x8E_ULCDRHlp+313c
Followup: MachineOwner
---------
quit
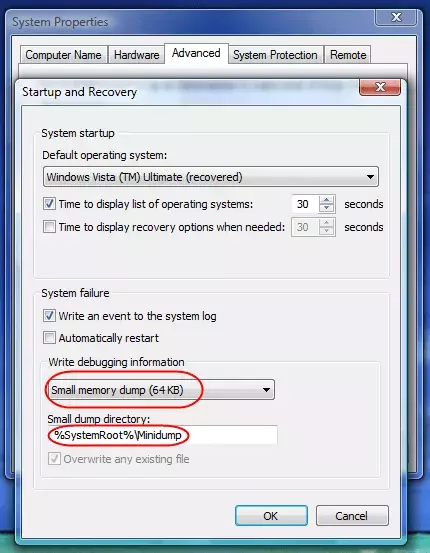

 Но вы можете сделать это самостоятельно, не прилагая больших усилий.
Но вы можете сделать это самостоятельно, не прилагая больших усилий.

 Но вы можете сделать это самостоятельно, не прилагая больших усилий.
Но вы можете сделать это самостоятельно, не прилагая больших усилий. ispatchRequestToDriver+0x533
ispatchRequestToDriver+0x533